Kepler – the russian web flooder
KEPLER – the russian web flooder of VDOS
“Those who have the privilege to know have the duty to act.”
― Albert Einstein
If you wonder how malicious actors find newly assigned address space to operate bullet proof hosting providers, keep reading!
We have been monitoring VDOS and other similar services for a few years now and trying to understand better this “pay-as-you-go attack industry”.
VDOS as the majority of the stress testing services make available some kind of application layer attack. Opposite to other types of attacks, application layer flooding requires a full TCP connection to operate. i.e. “real IPs”.
The most common application layer attack against websites is known as XMLRPC or “pingback attack” that uses third party WordPress Sites as reflectors. The attack is very common as it does not require the control of multiple compromised servers. A friendly hoster, making money renting out dedicated servers, that allows application layer floods is enough!
In order to perform this type of attacks, VDOS was launching specially crafted “pingback” requests against a list of WordPress websites. The WordPress websites, that are not operated by the attackers, are abused so as to act as a botnet against the victim.
With this attack one single IP address is able to generate hundreds/thousands of requests per second against the victim as coming from different locations.
For almost six months in 2016, VDOS has been using the IP space 185.103.252.0/23 to source the application layer attacks. During the six months of attacks, the IP space was announced by AS203466 “The Russian House Owners Association” with mail contact abuse@licitshield.com
Yes! Many cyber criminals are not shy about their operations. They can operate for months, cash in revenues and move to another setup with the very same hosting providers and upstreams.
The ASN203466 stopped the announcement of the 185.103.252.0/24 network the 12th of May 2016, when the prefix returned to the same LIR that allocated it to them: AS50113 Media Services Plus Ltd in Russia. Five months of operation.
It should not be a surprise that AS203466, have shared upstream providers with other malicious actors as the Sindicate Group responsible of scanning open resolvers for VDOS.
The two upstream providers are AS61272 INFORMACINES SISTEMOS UAB (Lithuania) and AS203912 SICRES SRL (Moldova).
So who is the “The Russian House Owners Association”?
Khlynovka-1 Association of property owners (aka Kepler) is a “house owners association” in Russia with address 1st Khlynovski sst., n. 10 in Kirov. The ТСН “ХЛЫНОВКA-1 – ОКВЭД: 70.32.1” is dedicated to the management and operation of houses. A company created to manage the house, utilities, etc. See registration document Kepler Registration Document
The association was crelated the 27th December 2015 and by the 11th of January 2016, traffic associated with the organization was visible from Moldova using Lithuanian and Moldovan upstream operators.
To our surprise, the organization changed their network description to “Kepler Infrastructure in Isle of Man” after two months.
Mobility is key, no shame, big gains.
As in the case of the Sindicate Group already reported in this site, cyber criminals are always on the move.
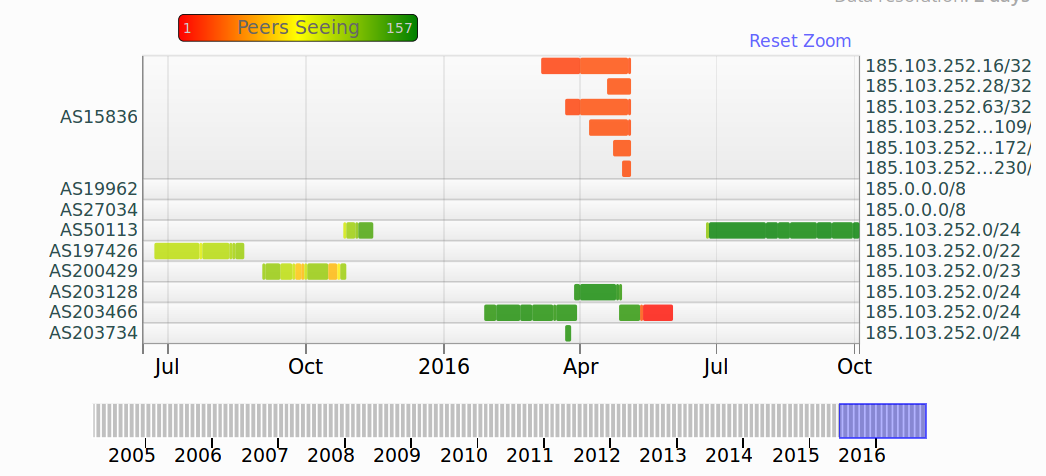
If we look into the history of routing announcements of Kepler’s network, we can see the first bogus announcements from AS197426 Bitcanal (Yes! more on this actor soon). Following the announcements of Bitcanal we can see how the network has been announced by Hostslim in the Netherlands but was not fully visible in all RIPE peers.
Timeline
- Kepler registers association in Russia the 27th December 2015
- Route object is created the 11th of January 2016,
- Kepler announces the network first time the 25th of January 2016.
- Kepler stops the announcement the 12th of May 2016
RIPE allocates the prefix 185.103.252.0/22
Prefix is allocated to AS50113 (LIR) the 10th June 2015 and its first announced by AS50113 the 27th of November 2015.
Other ASNs take over the prefix
As soon as the prefix was allocated by RIPE to Superservers in Russia, Bitcanal AS197426 started to announced the network the 23rd of June. The prefix was later announced by AS200429 Hostslim peering with AS197426 Serverius.
Kepler takes over. Mobility during six months in 2016
AS2o3466 Kepler – Association of house owners
AS203734 Pavel Bandaryk – Hostshield
AS203218 Sindicate Group
Return of the prefix to LIR
AS50113 LIR Superservers.
(Update 5th September 2016)
- Spamhaus has a report of the network here
- Virustotal reports malware in associated service lite.host l1h.net here
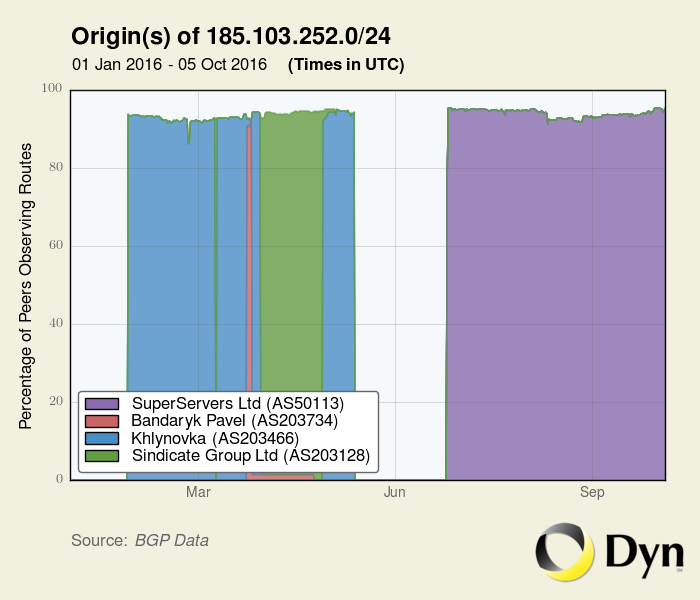
During the first phase the prefix was routed through Moldova (AS203734, AS203466 and AS203128) always transmitted through ARAX ISP (AS15836) and SICRES (AS203912).
Then (and now) it is routed out of Russia (AS50113).
BGP announcements … 174 (Cogent) 15836 203912 {203466, 203128, 203734}