Mirai runs hidden in dataflow.su
для чего ты используешь русский язык для Mirai, для того чтобы казаться более крутым хакером? Баклан!
From the past week, DOTSI AS49349 is announcing a totally new prefix 185.137.218.0/24. This prefix seems to be there only to re-announce one of the Mirai Command and Controls associated with the domain bklan.ru
Yesterday, one of our honeypots detected one attack from the Mirai bklan.ru botnet that was targeting the gambling site williamhill.com
Target: 141.138.130.12/32 Attack Type: GRE IP Attack Duration: 200 Time: 2016-11-01T15:17:14
This command and control has been moving a lot lately including locations at: Hostkey, OVH, BlazingFast and StormWall (under smart.antiddos.su/185.71.66.54).
There were a few interesting things of this domain that caught our attention
- Thew new command and control runs in port #23 at 185.137.218.161 (a newly announced prefix)
- The command and control is not issuing the banner “я люблю куриные наггетсы” but keeps the rest of messages in Russian.
пользователь: пароль: произошла неизвестная ошибка нажмите любую клавишу для выхода.
Who runs 185.137.218.0/24?
The prefix was first announced the 23rd of October using AS49349. (Update Dyn: First appeared 22:03:47 UTC on 22-Oct)
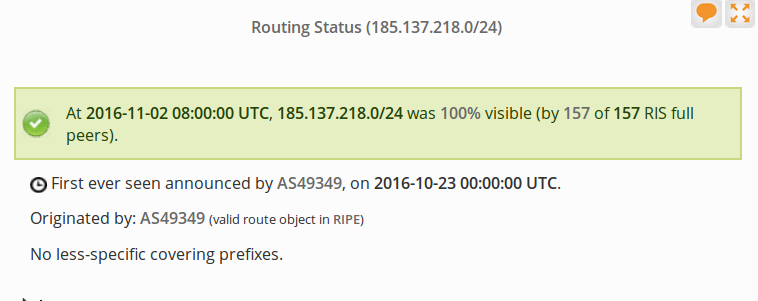
A quick review of all route objects shows newly created entities the 21st of October 2016. Here is a full copy of all objects
inetnum: 185.137.218.0 - 185.137.218.255 netname: FILTERNODE country: EU org: ORG-UN25-RIPE admin-c: DA7271-RIPE tech-c: DA7271-RIPE status: ASSIGNED PA mnt-by: FILTERNODE created: 2016-10-22T09:37:46Z last-modified: 2016-10-30T12:42:36Z source: RIPE organisation: ORG-UN25-RIPE org-name: UAB "Filtering Node" org-type: OTHER address: Italy, Milan abuse-c: NA5357-RIPE mnt-ref: FILTERNODE mnt-by: FILTERNODE created: 2016-10-30T12:38:59Z last-modified: 2016-10-30T12:38:59Z source: RIPE # Filtered person: Dmitriy Anavorskiy abuse-mailbox: filter.node@yandex.ru address: Kyiv, ul. Koubareva 33-a phone: +380937819182 nic-hdl: DA7271-RIPE mnt-by: FILTERNODE created: 2016-10-21T14:59:11Z last-modified: 2016-10-30T12:34:38Z source: RIPE
Where is Filternode?
Filternode is using AS49349 Dotsi to announce the network. The prefix seems reachable via Voxility infrastructure. What is really interesting is the latency changes that take place between Voxility and Filternode (+40 ms)
fra-eq5-01c.voxility.net 23.7ms fra-eq5-02sw.intranet.voxility.com 22.8ms ??? 185.137.218.161 66.4ms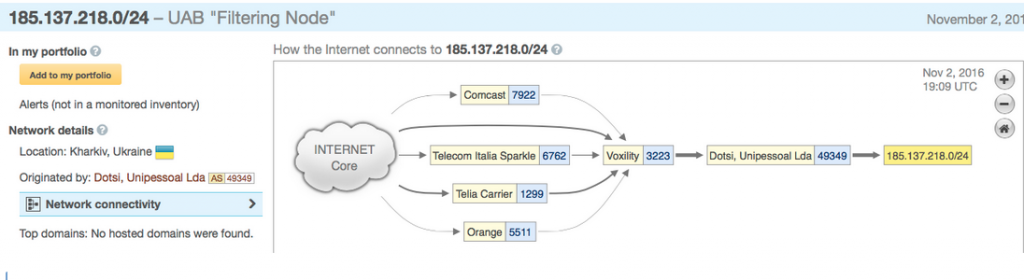
What is that “???”?
fra-eq5-02sw.intranet.voxility.com 23.7ms 46.172.91.220 66.8ms
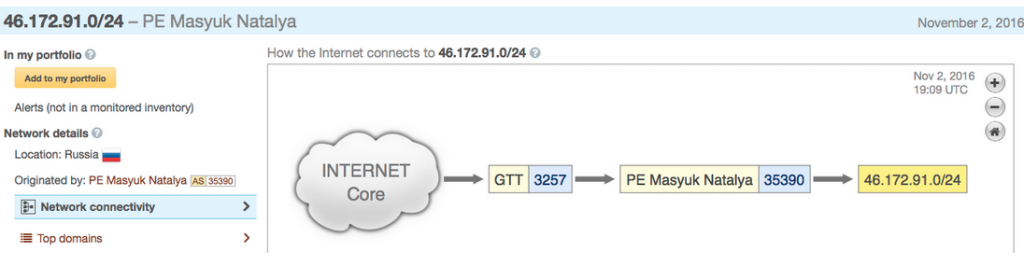
What we see is that the prefix is in fact announced via a tunnel (GRE most problably) with termination at 46.172.91.220
So ok, so from where is the prefix announced?
The prefix is announced from a provider known as MASYUK
inetnum: 46.172.91.0 - 46.172.91.255 netname: MASYUK country: RU org: ORG-PMN2-RIPE admin-c: MNI23-RIPE tech-c: MNI23-RIPE status: ASSIGNED PA mnt-by: MNT-MASYUK created: 2016-09-09T20:02:01Z last-modified: 2016-09-20T21:15:58Z source: RIPE
And who is AS35390 and Masyuk Natalya Ivanovna?
Judging by the official papers that can be downloaded here the ASN 35390 is allocated to “a grocery store”.
ПРЕИМУЩЕСТВЕННО ПИЩЕВЫМИ ПРОДУКТАМИ, ВКЛЮЧАЯ НАПИТКИ, И ТАБАЧНЫМИ ИЗДЕЛИЯМИ В НЕСПЕЦИАЛИЗИРОВАННЫХ МАГАЗИНАХ
Are you still there?
So let us recap, the domain bklan.ru that is used to control a large part of Mirai-based botnet is announced by a newly allocated network prefix 185.137.218.0/24 that is announced using a tunnel at IP 46.172.91.220 from AS35390. The registration papers points to a grocery store!
Who runs 46.172.91.220?
dataflow.su and the location of the tunnel seems consistent with a previous location of the server report.bklan.ru at 46.172.91.3
===
openssl s_client -connect 46.172.91.220:443 --- Certificate chain 0 s:/OU=Domain Control Validated/OU=EssentialSSL/CN=dataflow.su
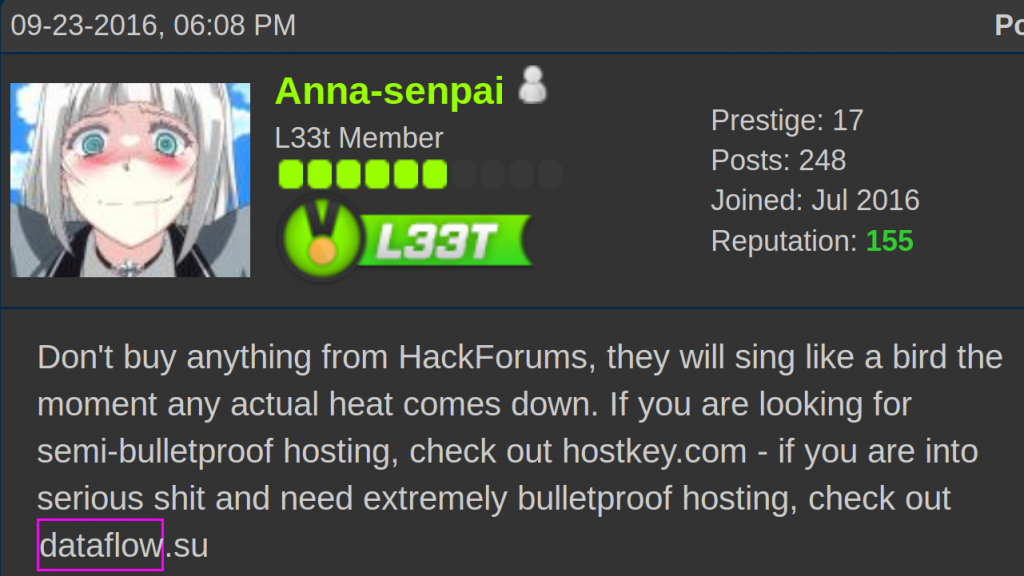
And what does Anna-Senpai thinks about dataflow.su?
Don’t buy anything from HackForums, they will sing like a bird the moment any actual heat comes down, if you are looking for a semi-bulletproof hosting, check out hostkey.com – if you are into serious shit and need extremely bulletproof hosting, check out dataflow.su
Info from dataflow.su
- Registered at Alpha Consulting (Belize) Ltd. New Horizon Building, Ground Floor 3 1/2 Miles Phillip S.W. Goldson Highway
Belize City. - RIPE info from dataflow.su here
- Alpha Consulting (Belize) has registered lots of companies including a few that appear in the Panama papers here

Dataflow and alfabank fraud
We have detected a fake SSL certificate of click.alfabank.ru hosted at dataflow.su IP address 46.172.91.24.
The certificate is self-signed using the name (c) 2016 GlobalSigns, Inc. It seems that the attackers at taken advantage of security issue affecting the real GlobalSigns as reported here.
We include a copy of the fake certificate.
Certificate chain 0 s:/C=RU/ST=MO/L=Moscow/O=AO Alfa-Bank/OU=(c) 2016 GlobalSigns, Inc./CN=click.alfabank.ru i:/C=RU/ST=MO/O=GlobalSigns Inc/OU=(c) 2016 GlobalSigns, Inc./CN=GlobalSigns CA 1 s:/C=RU/ST=MO/O=GlobalSigns Inc/OU=(c) 2016 GlobalSigns, Inc./CN=GlobalSigns CA i:/C=RU/ST=MO/O=GlobalSigns Inc/OU=(c) 2016 GlobalSigns, Inc./CN=GlobalSigns CA --- Server certificate -----BEGIN CERTIFICATE----- MIIEFDCCAvygAwIBAgIJAL7sJDWwrJHTMA0GCSqGSIb3DQEBCwUAMHIxCzAJBgNV BAYTAlJVMQswCQYDVQQIDAJNTzEYMBYGA1UECgwPR2xvYmFsU2lnbnMgSW5jMSMw IQYDVQQLDBooYykgMjAxNiBHbG9iYWxTaWducywgSW5jLjEXMBUGA1UEAwwOR2xv YmFsU2lnbnMgQ0EwHhcNMTYxMDI4MTE0MDA2WhcNMjcwMjAzMTE0MDA2WjCBgzEL MAkGA1UEBhMCUlUxCzAJBgNVBAgMAk1PMQ8wDQYDVQQHDAZNb3Njb3cxFTATBgNV BAoMDEFPIEFsZmEtQmFuazEjMCEGA1UECwwaKGMpIDIwMTYgR2xvYmFsU2lnbnMs IEluYy4xGjAYBgNVBAMMEWNsaWNrLmFsZmFiYW5rLnJ1MIIBIjANBgkqhkiG9w0B AQEFAAOCAQ8AMIIBCgKCAQEA6oHbqFjeuCuBTVocfwYGzSKWilS+eRqG4vG41S2Q tB/3nXwP4gdvtGELWMm1avbXAQkiIW0WJlTZw5wukrGheqBtOSwOhvTk/722fVgR AjfJyXCcMnMtt12wk3MQYM+9gaKf4sxowYnASpyf/NL8/+TF9Mbfap2O8uJRAip3 3KlaphZL1uDoNjN6Vrva15Mj7tihXQXaYfsacJjhBeGdMzOwSPZjNFshBhCi+jya 6ezoixx6hwtmRhyZdDBNuckfWg9NFNsb9wEA/tXGXN2knrITGdTnjG+vqIlG9hqt 9e2M33OhUTDELUHUTTFKTAqy3PR4NDkZnr2dmQ2pUmSgGwIDAQABo4GaMIGXMAkG A1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRp ZmljYXRlMB0GA1UdDgQWBBTiHEfWroKnsJIpIph5RuOZRAuhmjAfBgNVHSMEGDAW gBRlenkHq3462aJjvLw0mSGT3YBA0zAcBgNVHREEFTATghFjbGljay5hbGZhYmFu ay5ydTANBgkqhkiG9w0BAQsFAAOCAQEAJm0zMjILwZ+twhvrspZr/GhlKYyZcj2P W7KbhX2pO5kgTqW1k3BLUNKXJItJqcvVk+v+fdEOKL9Cmus5opGOOmEZdXmO5YH6 73OPxbe0Fs1nyleqYHuuQ9C83M1b6t8M2kR791NFQ9o6nqyMah5TNCXeZf8hxltU 2a9O6tB80Swsg1WlyA0iDw6bx5XvoZqM/YjGFKvlFGuhBUVElGlk1D3riWVJEgNs F4rrcgpQ5LGb2aNznnAwXAWVwnqYd0OgdDTiXD98/T31/4o8K84Ohe5UuwFMLJ2b qLbzUgH3j8XQbrwl7s4UQcwdOmuAc+em1fTSSfJhbPi2Uk50wOo5vw== -----END CERTIFICATE----- subject=/C=RU/ST=MO/L=Moscow/O=AO Alfa-Bank/OU=(c) 2016 GlobalSigns, Inc./CN=click.alfabank.ru issuer=/C=RU/ST=MO/O=GlobalSigns Inc/OU=(c) 2016 GlobalSigns, Inc./CN=GlobalSigns CA
LuaBoot is also hosted at dataflow.su
46.172.91.20, also in dataflow hosts samples of LuaBoot, another DDoS malware for the IoTs. The samples connect to the following locations
- 94.242.206.73:10419
- 31.184.234.154:8875
- bulutof.info
- iotsecurityresearch.info
Where is 46.172.91.0/24 coming from?
The prefix comes from AS203162, Balta Alliance that received the network 46.172.90.0/23 from AS43100.
2016-09-26 - 2016-11-02: 35390 - 46.172.91.0/24 * 2016-09-17: MASYUK-AS , UA 2016-06-15 - 2016-07-17: 203162 - 46.172.90.0/23 * 2016-07-13: BALTA-ALLIANCE-AS Balta network centre, UA * 2016-04-16: BALTA-ALLIANCE-AS BALTA ALLIANCE LP, UA 2016-06-08 - 2016-06-13: 43110 - 46.172.90.0/23 * 2016-04-16: ROSTNET-AS Joint Ukrainian-American enterprise Ewropol with legal form Ltd, UA 2016-01-01 - 2016-03-08: 43110 - 46.172.64.0/19 * 2014-03-29: ROSTNET-AS Joint Ukrainian-American enterprise Ewropol with legal form Ltd,UA
The following graph shows how the prefix 46.172.91.0/24 has been flapping frequently the 20-21st October.
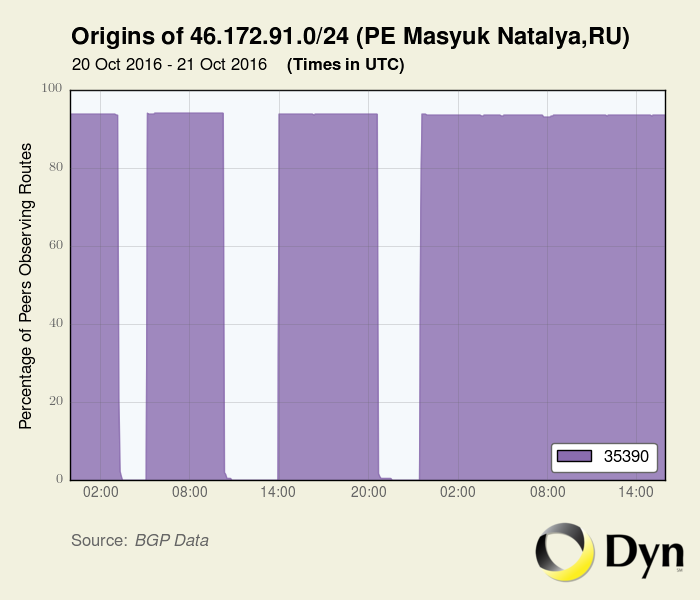
The first time this prefix was announced by AS35390 was the 2016-09-25 08:00:00 UTC.