Who is Rainbow?
During our investigation of VDOS stresser, we identified a very active account in the VDOS leaked logs published at Brian Krebs’ website.
RainSpai3n was at least responsible of 335 attacks including some .IL targets. Despite the claims from VDOS owners that the “stresser” was not attacking Israeli targets. The filter could be bypassed by adding :80 to the domain names when launching application layer attacks against the sites.
This is a sample of the IL sites that RainSpai3n attacked.
https://www.rubly.co.il:80 http://afula.muni.il:80 https://www.lbs.co.il:80 http://www.pcgalaxy.co.il:80 http://pcgalaxy.co.il:80 http://jetserver.co.il:80 http://drinkpoint.co.il:80 http://forum.pcgalaxy.co.il:80 http://www.textmagic.co.il:80
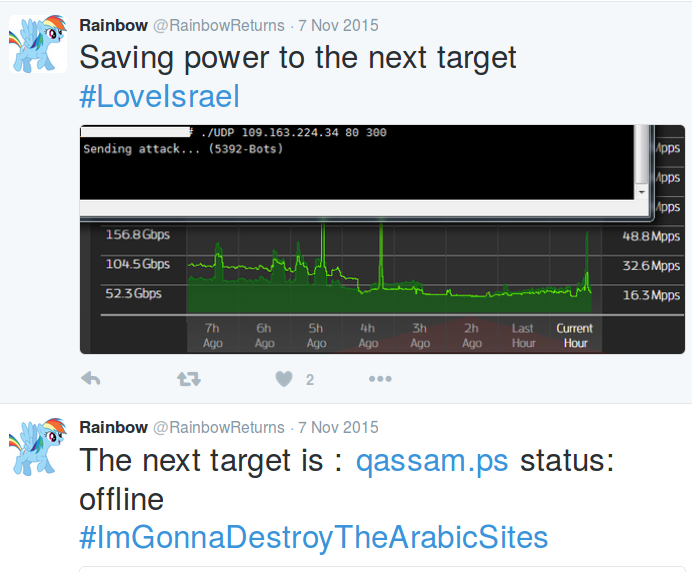
RainSpai3n also targeted the newspaper Haaretz the 2nd of Jul 2016 as shown in the target entry
16546097,'RainSpai3n','Launched a VIP stress test on 192.118.72.27:53 for 600 using ESSYN','79.179.123.26 (IL)','02-07-2016 12:04','Google Chrome v51.0.2704.103 on windows',0
The leaked RainSpai3n email account used the email jonatanmalker@gmail.com in the VDOS database. In archived files from Twitter we linked the mail to @almogsabah
Not until last week, when we looked closely into Proginter.com and the Pony Squad that we realized that the account “Rainbow” was linked to the stress testing service inboot-s.com that stopped working when VDOS was seized.
The linkage of almogsabah@gmail.com and Rainbow was also present in another stresser database leaked instress.club here
INSERT INTO `users` (`ID`, `username`, `password`, `email`, `rank`, `membership`, `expire`, `status`, `referral`, `referralbalance`, `testattack`, `activity`) VALUES (764, 'Rainbow', '9184669673a29d13a257cc404b7fccea3d85b397', 'almogsabah@gmail.com', 0, 6, 1454968800, 0, '0', 0, 0, 0),

Who is Almog Sabah?
As many other operators of stress testing services, Almog Sabah got interested in DDOS when playing Minecraft. One of the few postings of his work related to RGuard AntiDDoS v1.6, a system to defend against denial of service attacks, that Almog Sabah (אלמוג סבח) started with his friend Lior Aaron (ליאור אהרון).
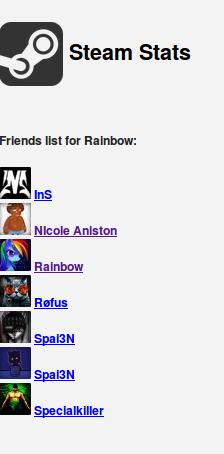

Almog Sabah uses the following identifiers almogbk, almogprobk, almogprobm, RainSpai3n, RainbowReturns, Rainbow Dash and Rainbow. In HackForums he uses the ID: 2373445
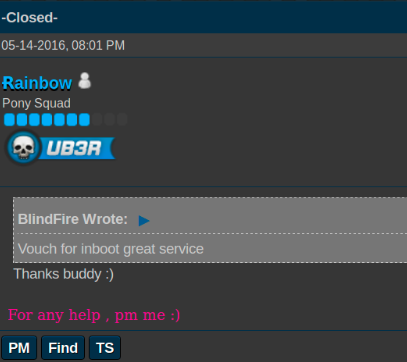
Almog Sabah and IDF support
Almog Sabah happens to be the brother of Sapir Sabah. Sapir Sabah became publicly known in Israel in 2014 when she sent a letter of complaint about her teacher, Adam Verete, to the Minister of Education, Shai Piron. The letter accused her teacher of presenting the Israel Defense Forces (IDF) as an immoral army and to teach “extreme radical views” which Sabah felt are inappropriate for a classroom.
The story of Sapir Sabah was widely covered in Israel here and here
An interesting outcome of our findings is to discover how stress testing services are not something uncommon for the Israeli youth and how such services are used not only to target gamers online but also newspapers and other media outlets.
Rainbow and booter.xyz (XyZBooter)
@RainbowReturns seems to have a very close connection with booter.xyz. In the following tweets, booter.xyz and @RainbowReturns celebrate attacks against Arab targets.
According to booter.xyz website their business is: “We are kind of legal ‘DDoS for Hire’ company”
Zenmate VPN
To hide his tracks, Almog Sabah often uses Zenmate VPN with servers in Voxility network in Bucharest (Romania)
Target list
We are providing a list of some of the targets we managed to identify. As you can see, there are a combination of gaming sites and a few newspapers. A special case is the attack against this article http://mizbala.com/news/111455. If anyone can give us more information of who is the “Shadow” and why the attacker is targeting that article, please let us know.
http://afula.muni.il http://at.al http://csgojingle.com http://drinkpoint.co.il http://hacalafula.co.il http://haaretz.co.il http://hapushtak.info http://jetserver.co.il http://manager.zare.co.uk http://mixlr.com http://mizbala.com/news/111455 http://pcgalaxy.co.il http://platgames.com http://pxlworld.com/battle/ http://spaly.net https://pxlworld.com/battle/ https://seaworld.com/ https://uk.godaddy.com https://www.aminoshop.co.il/ https://www.directadmin.com https://www.lbs.co.il https://www.pcgalaxy.co.il https://www.proginter.com https://www.rubly.co.il https://www.spaly.net http://www.djozrahamim.net http://www.hayokra.co.il http://www.imvu.com http://www.issta.co.il http://www.maveze.co.il http://www.pcgalaxy.co.il http://www.piner.co.il http://www.relog.co.il http://www.textmagic.co.il
Our talks with Rainbow
During the past week, we have been in touch with Almog Sabah to ask for his own explanations. Almog Sabah started by denying any involvement in the stress testing community in Israel to state later that: “I know what is “stresser” but not more.. i cant help you with that and i really want sorry”.
When asked why his account was part of the VDOS and other stress testers leaked databases, he told us that the IPs in the logs where not from his Internet provider. It was then that we could track how Almog Sabah changed his connection to a Zenmate VPN.
When asked why other documents online point to him as the operator of booter.xyz, he replied that “Its a israeli little kid thats hate me i talk with him to remove this bullshit and he said that he trying but he cant do it so ill speak with the site owner.”
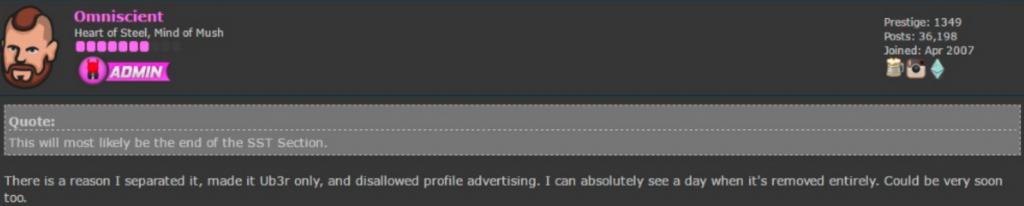
Booter.xyz remains operative but due to new restrictions in Hack Forums, booter.xyz is currently looking for someone with “Ub3r” status to announce the booter.