Bestbuy – VDOS reloaded
During the past six months we have been closely monitoring the development of the Mirai botnet and its connections with the Israeli stress testing service vdos-s.com.
This article summarizes ten of our findings:
1. Protraf wrote the Mirai code, but others also walked the walk
As already reported in January, Mirai was originally written by two members of Protraf, a hosting company not only specialized in protecting Minecraft servers but also engaged in all sorts of underground battles with competitors including launching denial of service attacks and routing hijacks.
During months we wondered what was the connection of Josiah White (Bashlite, Qbot) and Paras Jha (Anna-Senpai. Dreadiscool) and the largest botnet using Mirai. This very active botnet that later on became publicly known as “Botnet #14” was operated by someone that seemed to have close connections with the code owners but with the freedom of choosing its own targets.
Botnet #14 used the domain mufoscam.org as one of the earliest placeholders for the command and control.
While monitoring the different Mirai deployments, it became also obvious that this special actor had very special targets and interests. The victims were not just gamers playing call of duty, online dating websites or minecraft servers but mobile infrastructure inside Liberia.
By then we knew that following Mufoscam.org, was following Botnet #14. Monitoring route updates inside Liberia was monitoring Mirai in action.
2. VDOS – “the VIP DDOS market”
Thanks to the documents early released by drowzeepok and the analysis of hundreds of attacks launched by several stress testing services during the past couple of years, we understood that vdos-s.com backend (spoofing) servers were the common infrastructure used by many other “booters”, some of them also based in Israel and hosted in companies like Proginter.com and hidden behind Cloudflare.
If you want to read more how we tracked a few of them down, check the articles: Who is Rainbow? and Ponies in the Mist, stressit.org
3. The VDOS and Bestbuy VIP client connection
When Mirai started to attack a GSM operator in “Liberia”, we double checked again the VDOS leaked database, in the database we found records of a few interesting conversations between “bestbuy” and the VDOS support system back in late 2015. The support messages between bestbuy and the VDOS shows how Bestbuy wanted more powerful attacks from VDOS service against Liberia and he was willing to pay for them.
22-10-2015 13:32 bestbuy> Okay fair enough, I hope 50gbps is the actually speed for vip…
I’ll probably purchase soon. Thanks!’
22-10-2015 13:38 vdos> Hello bestbuy,
No problem, feel free to contact us again if you need any further assistance.
Best regards, P1st.
24-10-2015 13:19 vdos> Hello bestbuy,
Each stress test is between 20-100+Gbps using DNS (depending on running stress tests), this information is included in our Terms of Service.
May I ask why you require more power, 20-100Gbps should be enough to render most non-DDoS protected hosts offline.
24-10-2015 14:53 vdos> Hello bestbuy,
I cannot really assist you with this problem, sorry. If you provide me with an IP address and port, I will try to find a working method.
02-11-2015 07:55 bestbuy> 41.57.89.17
I’ll give it another shot soon, thanks for checking!
Yes, Just if you wonder: 41.57.89.17 is a Lonestar Cell address in Liberia.
4. Bestbuy, Cyprus and the other VDOS accounts targeting Liberia
A close review of the VDOS leaked database reveals that several accounts created in the VDOS’s stress testing service were operated from a Cyprus IP address. Attacks started at least in late 2015 and have been ongoing until early 2017. In an article published in this site in late December 2016, we already linked Cyprus IP addresses to attacks against the GSM operator: Lonestar Cell.
5. Anna-Senpai felt the heat. Source code is released
When Paras Jha (Anna-Senpai), felt the heat, he dumped the source code of Mirai in Hack Forums. This was not the first time that code of this nature has been dumped in the public domain. Qbot, a predecessor of Mirai also ended up in the Hacker Forum.
For reasons we still ignore, the code released by Paras Jha included the string “VDOS” in one of the botnet components that suggests that a Mirai deployment was rented to VDOS.
6. From Dyn, Spamhaus, Lonestar Cell to Deutsche Telecom
As many others monitoring Mirai, by following the whereabouts of the mufoscam.org, we could track a few large attacks that often used the GRE and DNS attack vectors. But in late November 2016, something unexpected happened. A new attack vector “made Mirai great again!”
The new attack vector was connected to the domain tr069.pw as the TR069 attack vector was used to enlarge the number of machines compromised by Mirai.
In preparation, Bestbuy provisioned two full networks to operate Mirai from Peterburg International Network aka PIN. The networks (5.188.232.0/24 and 5.8.65.0/24) were registered using the fake identity Bharath Kuchangi, BB9693-RIPE.
bestbuy registered the networks using an email from the domain novotele.online.
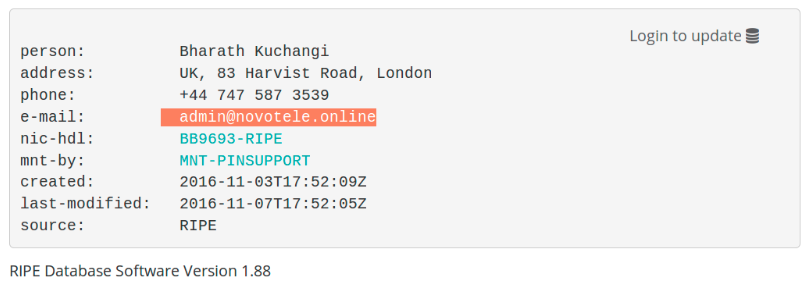
7. Bharath Kuchangi, a flexible identity
The details of Bharath Kuchangi were used to register Internet resources in RIPE where Peterburg International Network acted as a LIR proxy. Bharath Kuchangi identity was also used to obtain code-signing certificates. The data leak from Hacking Team shows that one of the certificates was in the name of Kuchangi. Bharath Kuchangi used the e-mail address fwd6ua@gmail.com in those certificates.
8. A very mobile command control
The Mufoscam.org botnet (Botnet #14) has been moving to a myriad of ASNs. Following this botnet has been a fantastic way to find the best places in the Interwebs.
Where has been Botnet #14? In alphabetical order.
BG AS200002 Kandi EOOD BG AS201640 MEGA - SPRED LTD BG AS20876 GEO KOMERS 97 EOOD BG AS44901 BelCloud Hosting Corporation DE AS20773 Host Europe GmbH DE AS47447 23Media GmbH LT AS61272 Informacines sistemos ir technologijos LV AS24651 JSC BALTICOM NL AS16265 LeaseWeb B.V. NL AS16265 LeaseWeb B.V. NL AS201630 Qhoster NL AS29073 Ecatel Network NL AS43350 NFOrce Entertainment BV NL AS49981 WorldStream NL AS62454 ZYZtm Research Division 10 B.V. RO AS3223 Voxility S.R.L. RO AS49349 BlazingFast RO AS57786 HOSTING TRIPLU W CONCEPT SRL RO AS60115 SC Klass Systems Grup SRL RO AS8708 RCS & RDS SA RU AS44050 Petersburg Internet Network ltd RU AS8219 ICExpert Company Limited US AS30186 Toqen LLC
9. Bestbuy, zero day exploits and denial of service attacks
One of the most fascinating aspects of Bestbuy is his good understanding of the “Market Place”. What better way to be close to the market that operating the market?
10. Who is bestbuy? Why a mobile operator in Liberia?
This morning, the Federal Criminal Police Office of Germany announced the detention of a suspect in Luton Airport in connection to Mirai and the attacks against Deutche Telecom. It seems that we might finally find out who bestbuy really is and why he targeted a place in Liberia.
Stay tuned for more updates and to find out who Bill Bones is and what Peter Parker does in the Internet.
As always, thanks for reaching out! Want to contribute? Reach out.