Harambe or not harambe!
Shame on you!
For the past twelve hours, the SpoofIT website has been suffering a series of denial of service attacks. The first attack was launched by @bannedoffline from 178.251.228.80. The application layer attack is using a tool known as Hulk.
The first attack was launched from AS30823 Combahton IT Services the evening of the 17th of October 2016.
@BannedOffline, that claimed in the past being part of the attack against Brian Krebs, launched a HTTP flooding attack against this site from one of the servers that is also using for the protection of the Ghost Squad Hackers anti-ddos site ddos-shield.biz
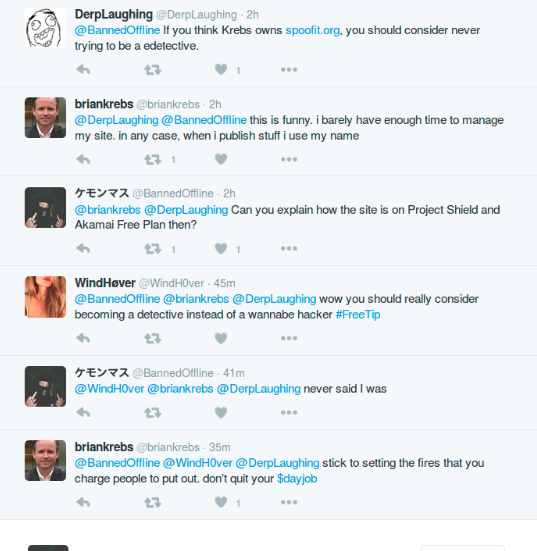
For the attack @BannedOffline is using the IP 178.251.228.80. This IP hosts ddos-shield.biz, a project operated by @BannedOffline. In HackForums, @BannedOffline requests to attack the same IP to test his setup.
A sample of the flooding request that reassembles Hulk DDOS tool looks like
178.251.228.80 - - [17/Oct/2016:20:41:36 +0000] "GET /?6xd=PpDXrT HTTP/1.1" 405 568 [378] "-" "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 5.1; Trident/4.0; WOW64)" "---" "DE" "AS30823 COMBAHTON combahton IT Services UG (haftungsbeschraenkt)"
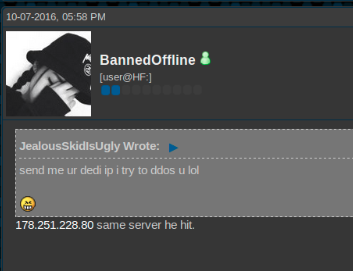
What is going on with those Ponies?
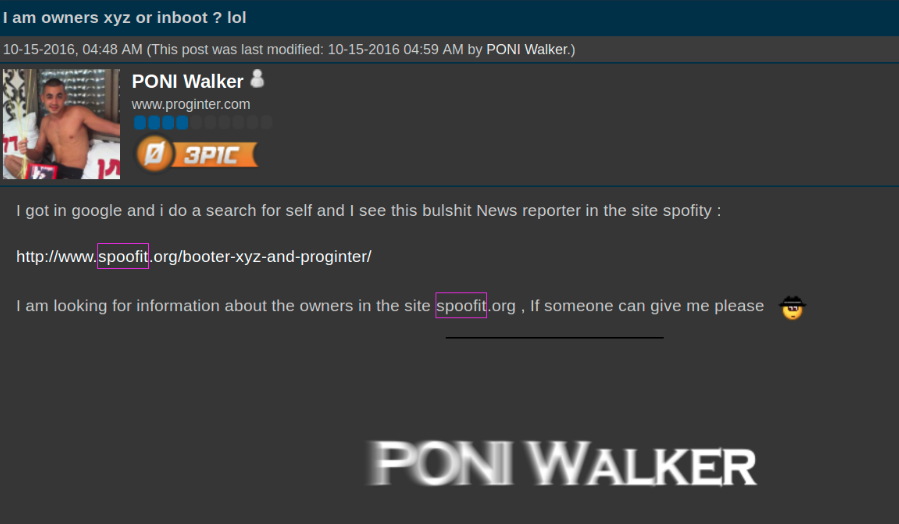
About the same time that the attacks started, the owner of Proginter.com that in another article we have linked with booter.xyz, has kindly requested us to remove any connections of Proginter.com with booter.xyz in this article.
Eden Hen, owner of Proginter.com has reached us a few days ago to clarify his role in the hosting of booter.xyz.
During our email exchange, Eden is trying to provide tangible evidence that he is not connected with Poni Walker. According to Eden Hen, Poni Walker is not working for him and he is deliberately using his company’s image just to gain attention.
When asked about booter.xyz, Eden Hen (CEO of Proginter.com) has confirmed that he has hosted the Stress Testing Service in the past but he removed as soon as he was “notified”.
More details on this, soon!
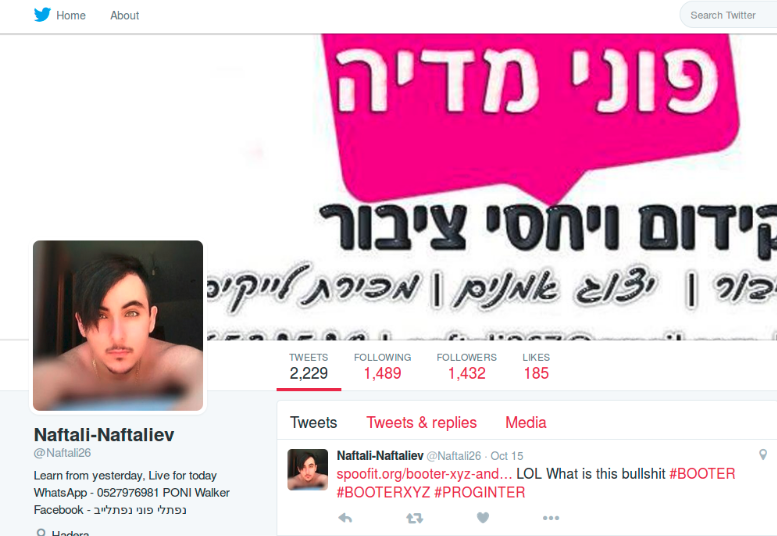
The second wave of attacks is using a ~ 3000 IP dedicated botnet with a large footprint in China (> 80%). At 12.00 PM UTC the attack is still active.
Samples of the requests look like:
GET /harambe HTTP/1.1 HOST: spoofit.org X-Forwarded-For: 120.214.244.242 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Linux; Android 5.0.2; LG-V410/V41020c Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/34.0.1847.118 Safari/537.36 Cache-Control: no-cache
The user agents used by the botnet follows:
Mozilla/5.0 (Linux; Android 4.2.2; AFTB Build/JDQ39) AppleWebKit/537.22 (KHTML, like Gecko) Chrome/25.0.1364.173 Mobile Safari/537.22 Mozilla/5.0 (Linux; Android 4.4.3; KFTHWI Build/KTU84M) AppleWebKit/537.36 (KHTML, like Gecko) Silk/47.1.79 like Chrome/47.0.2526.80 Safari/537.36 Mozilla/5.0 (Linux; Android 5.0.2; LG-V410/V41020c Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/34.0.1847.118 Safari/537.36 Mozilla/5.0 (Linux; Android 5.0.2; SAMSUNG SM-T550 Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/3.3 Chrome/38.0.2125.102 Safari/537.36 Mozilla/5.0 (Linux; Android 5.1.1; SM-G928X Build/LMY47X) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.83 Mobile Safari/537.36 Mozilla/5.0 (Linux; Android 6.0.1; Nexus 6P Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.83 Mobile Safari/537.36 Mozilla/5.0 (Linux; U; Android 4.2.2; he-il; NEO-X5-116A Build/JDQ39) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Safari/534.30 Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36 Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36 Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36 Mozilla/5.0 (Windows Phone 10.0; Android 4.2.1; Microsoft; Lumia 950) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/46.0.2486.0 Mobile Safari/537.36 Edge/13.10586
A sample of the IP addresses of the botnet follows, please let us know if you know anything about it!
ISO IP ADDRESS AS NAME ========================================= CN 101.17.183.26 4837 CN 101.17.184.160 4837 CN 101.17.225.23 4837 CN 101.18.190.172 4837 CN 101.18.52.117 4837 CN 101.19.233.37 4837 CN 101.19.41.250 4837 CN 101.20.153.238 4837 CN 101.20.187.25 4837 CN 101.20.210.87 4837 CN 101.20.223.7 4837 CN 101.20.91.41 4837 CN 101.21.153.208 4837 CN 101.21.21.143 4837 CN 101.21.255.89 4837 CN 101.22.223.153 4837 CN 101.22.38.151 4837 CN 101.22.85.49 4837 CN 101.23.157.246 4837 CN 101.23.71.194 4837 CN 101.23.99.57 4837 CN 101.24.116.178 4837 CN 101.24.250.79 4837
Another botnet joining the attack?
A second botnet is now part of the attack. The attacks is a WordPress XMLRPC Reflection attack composed of ~2600 new servers. The attack is sourced by one single server hosted at AS64484
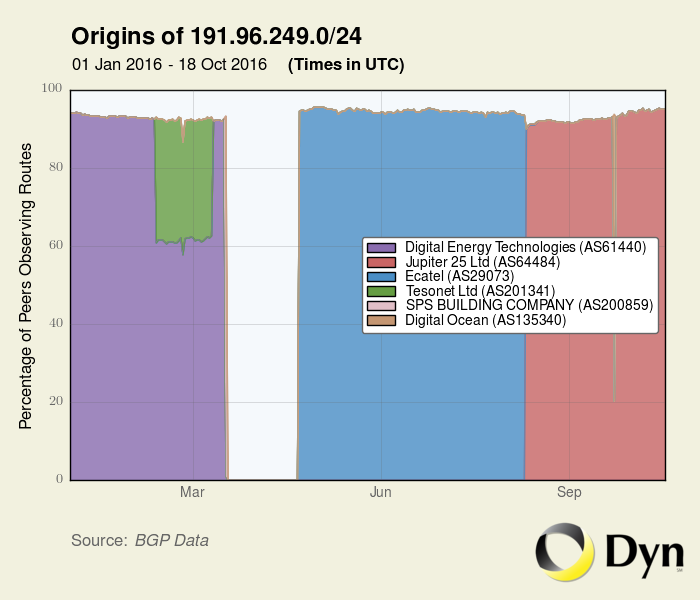
2016-09-23 - 2016-10-17: 64484 - 191.96.249.0/24
2016-09-01: ASDMZHOST , NL
2016-09-22 - 2016-09-22: 135340 - 191.96.249.0/24
2016-04-15: DIGITALOCEAN-AS-IN Digital Ocean, Inc., US
2016-08-10 - 2016-09-21: 64484 - 191.96.249.0/24
2016-09-01: ASDMZHOST , NL
2016-04-21 - 2016-08-09: 29073 - 191.96.249.0/24
2016-07-13: QUASINETWORKS , NL
2016-04-16: QUASINETWORKS Quasi Networks LTD., NL
2016-03-17 - 2016-04-20: 61440 - 191.96.248.0/21
2016-04-08: Digital Energy Technologies Chile SpA, CL
2014-03-29: Digital Energy Technologies Chile SpA,CL
2016-03-16 - 2016-03-16: 200859 - 191.96.249.0/24
2015-03-26: SPSBUILDING "SPS BUILDING COMPANY"LTD,BG
2016-02-18 - 2016-03-15: 61440 - 191.96.249.0/24
2014-03-29: Digital Energy Technologies Chile SpA,CL
2016-02-11 - 2016-02-17: 201341 - 191.96.249.0/24
2014-11-21: TESONET Tesonet Ltd,LT
2016-01-01 - 2016-02-10: 61440 - 191.96.249.0/24
2014-03-29: Digital Energy Technologies Chile SpA,CL
Following our mission of exposing the hosting companies and carriers enabling these attacks, I asked where prefix 191.96.249.0/24 is currently sourced.
Wait for it! The upstream provider of AS64484 is…. Ecatel!
And by the way, in the same network could be found in the past the domain name server for amplists.com, used by VDOS to build their DNS amplification attacks.
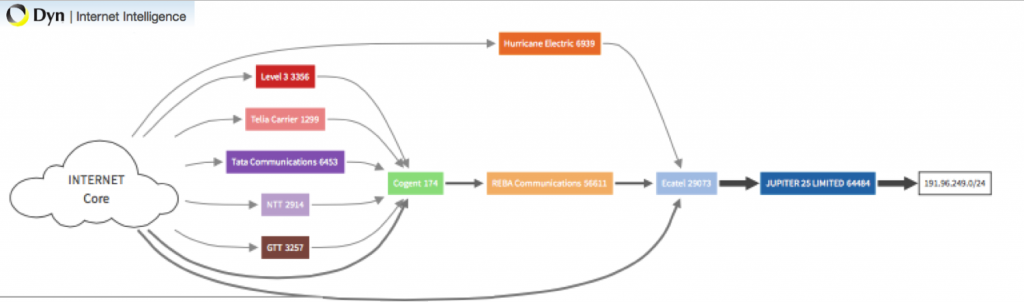
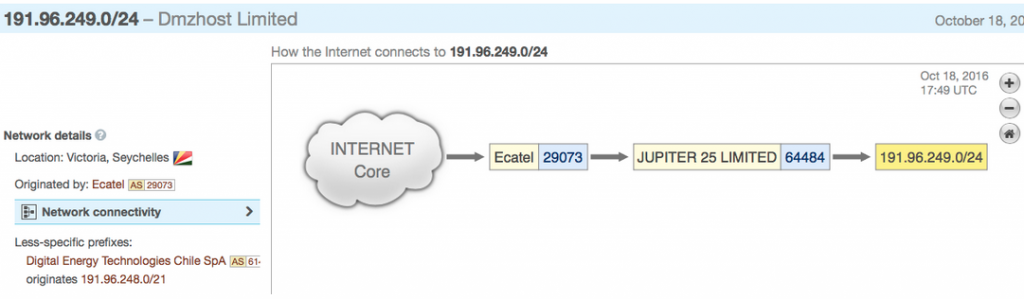
And here a much nicer representation of the prefix “mobility”. The network has been on the move constantly as described in another article. (Check the section, Let’s move it, move it)
The IP space seems to host servers from protonhost.net, a bullet proof hosting

Updated 19th October 2016
The attack has remain active for 24h now. Sample of the current flooding requests
39.89.29.60 - - [19/Oct/2016:10:37:45 +0000] "GET /sup HTTP/1.1" 200 178 [395] "-" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36" "---" "CN" "AS4837 CNCGROUP China169 Backbone" 120.52.94.54 - - [19/Oct/2016:10:37:44 +0000] "GET /sup HTTP/1.1" 200 178 [442] "-" "Mozilla/5.0 (Linux; Android 5.0.2; SAMSUNG SM-T550 Build/LRX22G) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/3.3 Chrome/38.0.2125.102 Safari/537.36"