Spiderman – A spot in the net
In our previous articles [1] [2] and [3], we have published how we linked the “Mirai botnet” with the Israeli stress testing service vdos-s.com. During this research we also discovered that the operator of the largest Mirai-based botnet has also been involved in other types of cybercriminal activities for years.
Now that the name of Daniel Kaye, pronounced Daniel Hai (חֵית) has been announced as part of the German investigation, it is time to review our initial findings and the current open questions in this case.

Very little information has been released to the public about the ultimate motivations behind the Denial of Service attacks against Liberian operator Lonestar Cell.
The only public statement is that: he had taken on the commission for a fee of $10,000 because he wanted to marry his fiancée and needed money for a “good start into married life”.

We have no doubts that 10.000 USD is not the “Real Deal” :). Let us continue our previous article in the place we left it.
10. Who is bestbuy/spdr? Why a mobile operator in Liberia?
The German case against “Daniel” focuses on how he took over thousands of routers of Deutche Telecom to increase the power of the botnet. It is important to know that even before Mirai was created (as an evolution of Qbot), the users “bestbuy”and “bestbuy2” were already using the services of VDOS-S to launch attacks against the Liberian ISP.
He connected to the service using addresses from the UK and Hong Kong where his fiancée has family members. We also found a user targeting the Liberian operator with the name starscell@mailinator.com, connecting from Cyprus.
As we already reported in this website, these attacks started even before Mirai was ever deployed using VDOS-S services including their premium VIP botnets.
How long he has been around using VDOS-S? we found record of spdr01@gmail.com (bestbuy) and parkajackets@gmail.com (bestbuy2) from November 2015… so definitely not one-time-shoot.
We still believe that understanding the attacks of Liberia and who order them is key to understand the wider implications of this case. Is this a 10.000 USD job? Is this just a kid alone in the Net? Judging by his connections in Linkedin, it seems does not is not the case.
11. Mirai needed more power to keep a special client happy
According to the public information available, Daniel hijacked Deutsche Telekom routers because he needed more firepower for his DDoS botnet. That “Mirai” was loosing DDOS-power was known to many InfoSec researchers. Several groups were systematically tracking the command and controls and reaching out to the different ISPs to suspend the servers or blackholing their domain names.
More bots were needed and also a stable command and control.
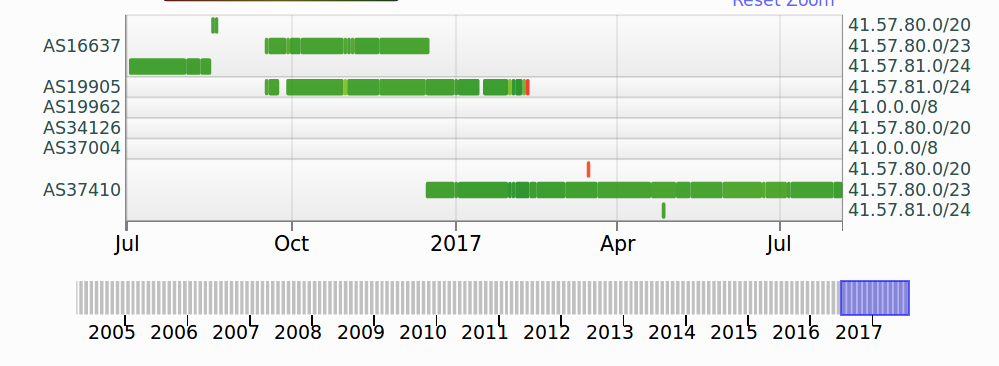
The outage of Deutsche Telekom that took place on the Sunday, November 27th, 2016 had an “interesting infrastructure supporter”. The command and control of Mirai was hosted in Petersburg Internet Network ltd. aka PIN since early November. For example, the domain rep.securityupdates.us was hosted in the 5.188.232.0/24 network from the 7th of November.
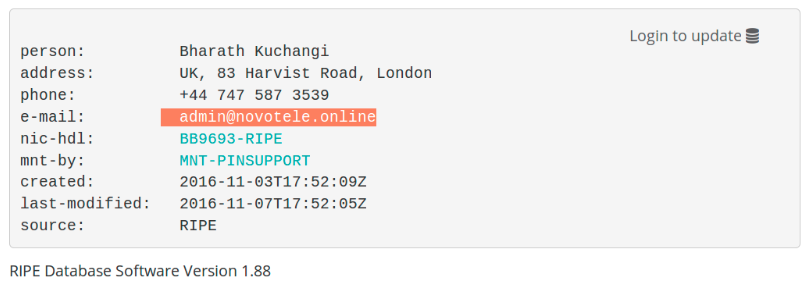
It is interesting to notice that PIN allocated IP space for our superhero using bogus personal information. “Spdr” used the details of “Bharath Kuchangi” to register Internet resources in RIPE where Peterburg International Network acted as a LIR proxy.
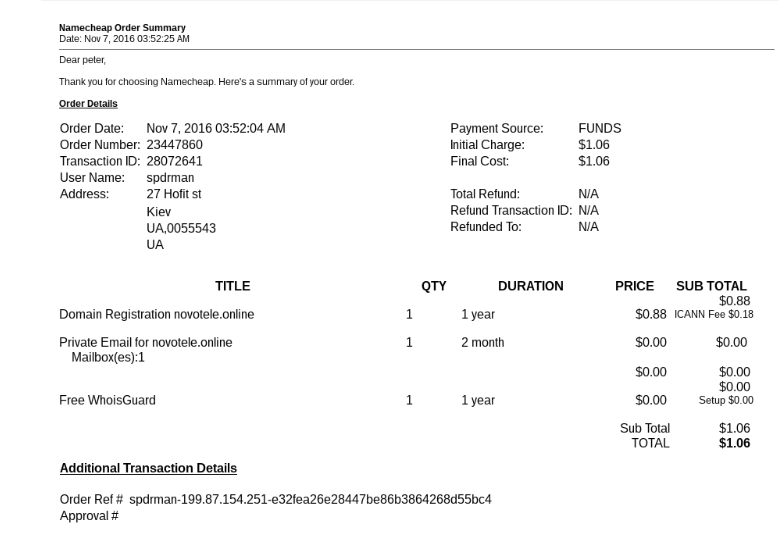
Back in November 2016, we already spotted how the domain novotele.online was used to register these IP resources in RIPE and gave us a few hints of “spdrman” whereabouts and possible next moves.
To our knowledge this is the first time we have seen several /24 networks allocated to keep a command and control alive in a DDOS-botnet setup. It was obvious to us that “spdr” felt very comfortable buying VPSs in bullet proof hosters but we never expected that new IP space was going to be allocated for just keeping this business alive.
In preparation for the Deutsche Telekom move, “Spdr” provisioned two full networks to operate Mirai from Peterburg International Network aka PIN. The networks (5.188.232.0/24 and 5.8.65.0/24) were registered using the fake identity Bharath Kuchangi, BB9693-RIPE.
These /24 networks were registered using an email from the domain novotele.online.
12. The “Eden Family”, spdr and Victoria Peak link
One amazing aspect of this case is that spdr01@gmail.com email has been associated to GovRAT since 2014. No hard core stuff, no dark web… a standard gmail mail box.
Why did it take three years to find the person behind it?
Let us quickly summarize the twenty steps we followed to find Daniel Kaye aka Peter Parker, Bill Bones, Spdr, Bestbuy…
- Reverse engineer the command and control of Mirai botnet as soon as we got a sample and published it.
- Tracked each of the command and controls used to launch attacks and recorded each of the victims.
- Identified the largest actor launching attacks: using the domains rep.securityupdates.us and mufoscam.org.
- Discovered that the command and controls were overlapping in previous malicious activity associated to the malware GovRAT.
- Identified spdr01@gmail.com as GovRAT author and member of BinaryVision discussion forum in Israel.
- Identified spdr01@gmail.com as interested in 0-days and GSM interception devices.
- Tracked two different emails were associated to GovRAT, spdr01@gmail.com and parkajackets@gmail.com
- Spdr01@gmail.com email was used to register the domain edenfamily.net, makovamirdavid.com and xn--7dbhugnk8ak.com. Historical records point to Kfar Saba in Israel and R. Eden.
- Singh Aditya, using the email address parkajackets@gmail.com to produce self-signed malware for GovRAT.
- Bharath Kuchangi, using the email address fwd6ua@gmail.com was used to register Mirai domains and RIPE IP resources with PIN.
- Found Kuchangi in the Hacking Team data leak
- VDOS database leak shows spdr01@gmail.com, bestbuy, bestbuy2 and parkajackets@gmail.com associated
- Found out that bestbuy and spdr01 used IP addresses from UK and Hong Kong to launch the attacks against Liberia GSM operator Lonestar Cell with the technical support from VDOS-S. We also saw BGP routing changes in Lonestar Cell to scrub the bad traffic using Neustar network/MTN
- starscell@mailinator.com from Cyprus runs attacks against similar targets. Linked Cyprus with UK and Hong Kong Activity.
- Found early reports of Liberia Telecommunication Authorities reporting about DDOS attacks.
- Shay Eden from the edenfamily.net has a social contact of the same age with a picture of Victoria Peak @ Hong Kong and with links to Katzanelson High School
- Gravatar account in social media uses the ID spdr and email danielkaye02@gmail.com
- Daniel Kaye is a common friend of S. Eden and D. Eden from the site edenfamily
- Daniel Kaye girlfriend C.M. has domain registered in Egham as Daniel family members E.J.K
- The owner of the Real Deal Market Place (bestbuy) trdealmgn4uvm42g.onion is interested in GSM interception and uses XMPP accounts bestbuy@creep.im and bestbuy@exploit.im
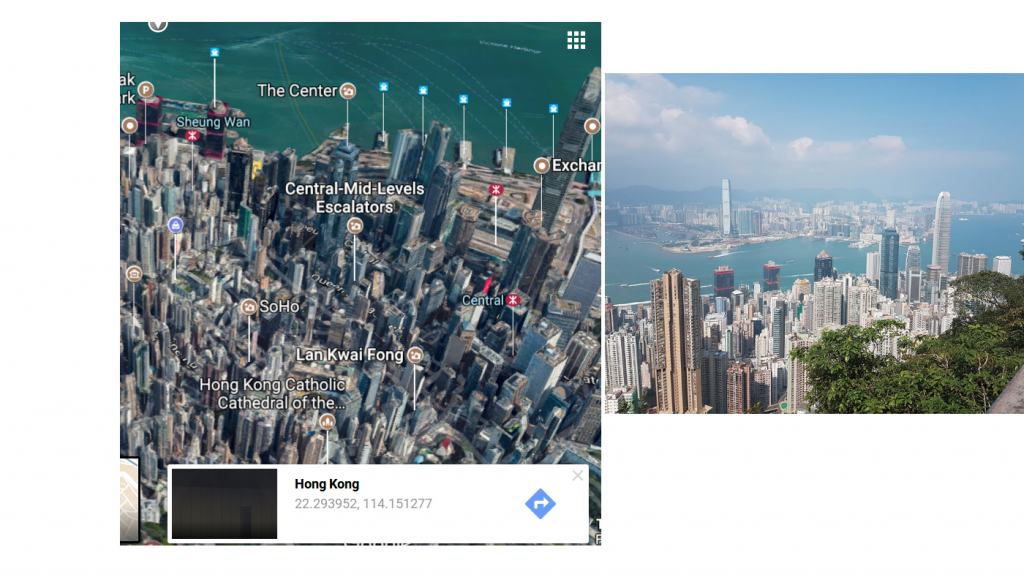
Victoria Peak – Hong Kong. Picture from Daniel Kaye (right)
So the question still remains? Who order these attacks and why?
Daniel said that he was hired by a Liberian ISP to carry out DDoS attacks on local competitors. I guess that gives us very little candidates to choose from.
- Did Peterburg International Network helped our superhero to keep his business alive?
- Why Bharath Kuchangi identity was used to register those RIPE resources?
- Which competitor of Lonestar Cell hired Daniel and why?
- Is 10.000 USD a good start into married live?
- Is four years of these type activities just a mistake?
How many GSM operators are in Liberia?
Lonestar Cell-MTN: Founded in 2000 by Beirut-based Investcom, a subsidiary of MTN Group since 2006. Liberian businessman Benoni Urey is the Chair of Lonestar Communication Corporation and owns a significant portion of the company through his PLC Investments Group.
Novafone-Libtelco: Currently owned by Libtelco, the former Liberia’s National Telecommunication Operator. (May 2016)
(Update 25th August 2016): A contributor has reported that Novofone was not purchased by Libtelco and that the company finally it was purchased by MTN [Novafone #1] and [Novafone #2][Lonestar #1] (May 2016)
Cellcom-Orange: Acquired by the Orange Group via its Orange Cote d’Ivoire. (April 2016)
The attacks recorded against Lonestar Cell in VDOS start in July 2016. Mirai targeted mostly Lonestar Cell-MTN and later on Novafone also know owned by Lonestar.
Cellcom-Orange was never targeted by Mirai.
Lonestar Cell, with support from the MTN Group, start using the services of Arbor International to mitigate the attacks from September 2016.
Want to read our previous articles?
- Ten things we learned from Mirai http://www.spoofit.org/bestbuy-vdos-reloaded/
- Mirai and the attacks against Lonestar Cell http://www.spoofit.org/mirai-and-the-attack-against-liberia/
- Mirai runs hidden in dataflow.su http://www.spoofit.org/mirai-hidden-behind-dataflow/