The 665 Gbps attack on “Krebs On Security”
In May 2016, a new member of GSH become specially active “@BannedOffline” in social media. @BannedOffline openly started to provide technical advice on defense and offensive techniques to other members of GSH. “@BannedOffline” collected third party tools and also methods in how to launch attacks and protect websites against Denial of Service. He is specially interested in exposing how simple is to take protected websites down and at the same time that he can build better DDoS protections that large vendors.
C Code” released under @BannedOffline revealed that he was not a coder as he took existing code from tH3j3st3r and claimed as his.
An interesting finding was to see how this group of attackers were taking advantage of multiple CDN services to maintain their infrastructure online. Rather than relying on typical providers such as “Cloudflare” or “Incapsula” to protect their sites and stress testers, a collection of documents from @BannedOffline described in detail how to use other third party CDN services. The “DDOS strategies” document describes creative ways to daisy chain them to hide the real location of the proxied services.
The method proposed by @BannedOffline to GSH was used with several of their domains. Paradoxically, GSH sites have been hosted behind Akamai CDN and Google cloud services. This strategy was also reported by Radware in early September including references to @BannedOffline.
The attack against krebsonsecurity.com of the 22nd of September did not fit into any of the traditional targets of GSH . Their attacks in the past did focus on a few large media outlets (CNN, Fox) and large banks. @BannedOffline seemed more interested in targeting several anti-DDOS providers to show the capabilities that he had control of. @BannedOffline did not follow the same modus operandi that other GSH members with clear focus on defacements and data leaks.
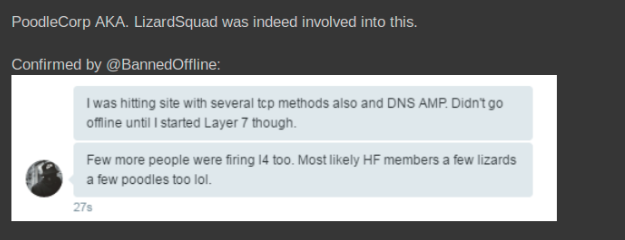
@BannedOffline, knows that volumetric attacks using reflection methods such as NTP, SSDP or DNS are easy to mitigate by anti-DDOS providers with large mitigation infrastructure and the main methods to take websites down require application layer attacks that bypass mitigation and reach the hidden protected servers (origins).